Cryptography
What cryptography does Bitcoin use?
Cryptography is the practice and study of techniques for secure communication in the presence of adversarial behavior.
Bitcoin uses cryptography. That's why it's sometimes referred to as a "cryptocurrency".
You might think that being a "cryptocurrency" means there's all kinds of cryptography flying around under the hood, but the Bitcoin software is actually built using two specific tools from the cryptographic toolbox:
1. Hash Function
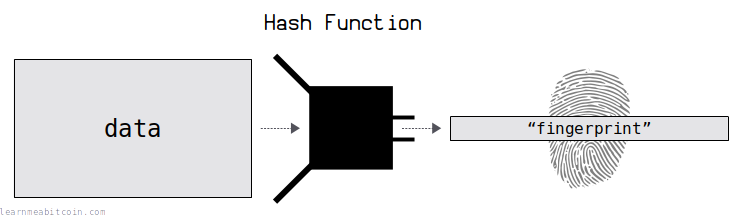
A hash function is a tool that creates fingerprints for data.
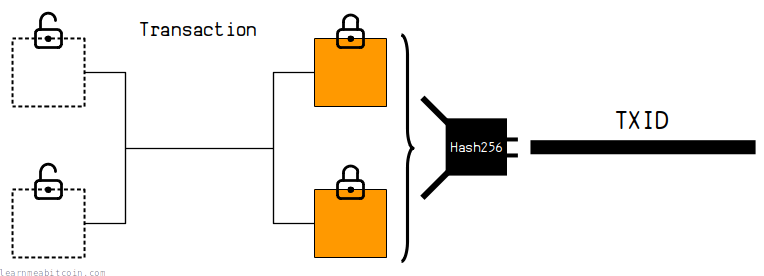
It takes in any amount of data, and scrambles and compresses it to produce a short, unique result called a "hash". And because these "hashes" are unique for each piece of data, they're perfect for use as reference numbers.
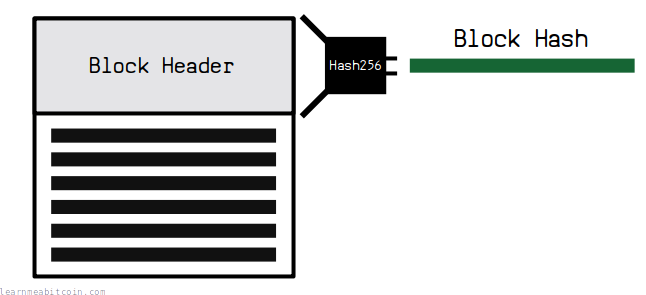
For example, we hash transaction data to create TXIDs, and we hash block data to get block hashes. This gives us unique references for each transaction and block, which we can use to look them up in a blockchain explorer.
Furthermore, every transaction is connected to a block through a merkle root, and every block is connected to another block by referencing the hash of a previous block.
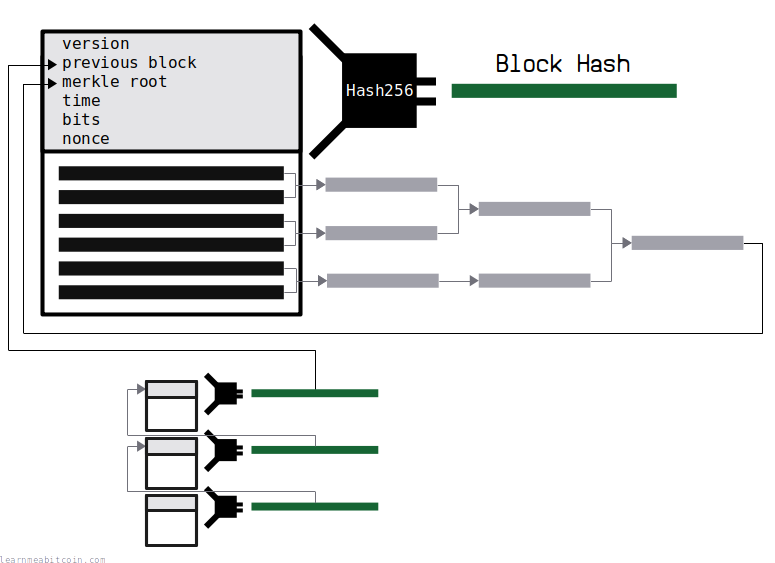
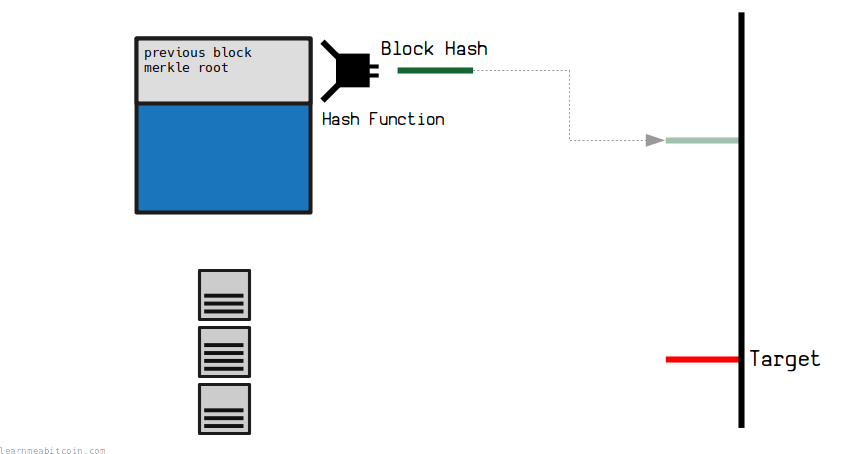
But what makes Bitcoin an invention is that Satoshi came up with the idea to use a hash function as the basis for mining.
In short, the result of the hash function is uncontrollable; you don't know what the result of the hash function is going to be until you actually hash the data. Satoshi used this property to create a form of lottery, where a new block can only be added to the blockchain if someone is able to get a block hash below a certain target value.
This means that no single person/computer is ever in complete control of the blocks that get added to the blockchain. This is what separates Bitcoin from all other payment systems created in the past, because for the first time ever there is no central authority in control of a ledger of transactions.
So whilst hash functions are used throughout Bitcoin as a general tool for creating reference numbers and linking data together, it's ultimately the clever use of the hash function for mining that sets Bitcoin apart.
Anyway, there are various flavors of hash function you can use, but Bitcoin uses the following two exclusively:
- SHA-256 (2001) – The primary hash function used throughout Bitcoin.
- RIPEMD-160 (1996) – A secondary hash function, only used for shortening public keys.
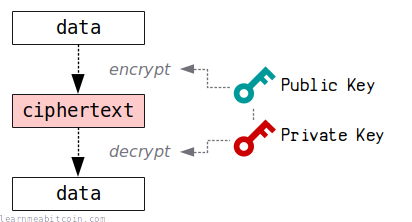
2. Public Key Cryptography
Public key cryptography involves using mathematics to create a pair of keys: a private key and a public key.
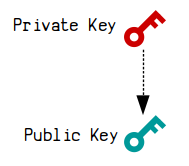
These are basically two very large numbers. And due to the special cryptographic mathematics used to create these keys, you can give away the public key, but nobody can work backwards from it to figure out the private key.
This isn't particularly useful on its own. However, part of public key cryptography is the ability to use the private key to create what's known as a digital signature, and this will also have a unique mathematical connection to the public key.

Anyway, Bitcoin utilizes this kind of public key cryptography as the basis for the locking mechanism inside transactions:
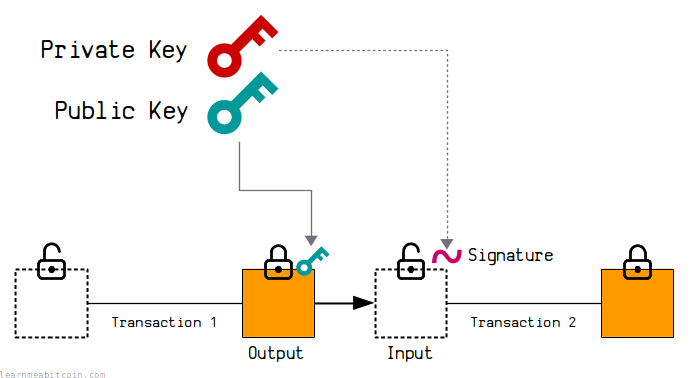
When you want to "receive" bitcoins, someone will create a transaction that locks a set amount of bitcoins (an output) to your public key.
Then, when you want to "send" these bitcoins to someone else, you create a digital signature using your private key, and this unlocks the bitcoins so that you can send them on to someone else.
Now, there are two properties of digital signatures that are vitally important for this to work:
-
Only the person who owns the private key for a public key can create a valid digital signature for it. This means that nobody can unlock your bitcoins unless they have the private key for the public key that the bitcoins have been locked to, because only the owner of the private key can create a digital signature that will have a mathematical connection to the public key.
-
A digital signature is created by using the private key to "sign" the entire transaction. This means that nobody can reuse your digital signature to unlock bitcoins locked to the same public key in a different transaction, because the digital signature itself is "tied" to the transaction.
So in short, Bitcoin utilizes this type of public key cryptography as the basis for securely controlling the ownership of bitcoins, and it all works thanks to the clever use of mathematics.
Anyway, there are various flavors of public key cryptosystems you can use, but Bitcoin uses the following two exclusively:
- ECDSA (1998) – The first public key cryptosystem used within Bitcoin.
- Schnorr Signatures (1990) – A more efficient alternative to ECDSA. The patent for this cryptosystem expired in 2010 (a year after Bitcoin was first released). It was integrated into Bitcoin as part of the Taproot upgrade in 2021.
Brief History
I'm not a cryptography expert, but it's interesting to a know a little about the history of public key cryptography so you know where Bitcoin stands in the grand scheme of things…
Public key cryptography has been around since the 1970s.
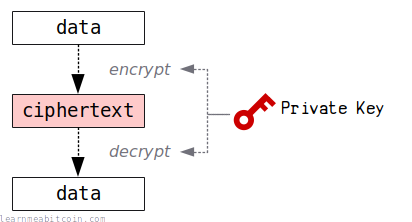
Before this, data could only be encrypted and decrypted using the same key (symmetric encryption). This worked well, but the problem was that you had to share the same key between two people, which was a nightmare for security, as it's difficult to share a single key without someone else getting their hands on it.
Public key cryptography solved this problem by allowing you to use a pair of keys (asymmetric encryption) instead. Now you can hand out a public key for people to encrypt data with, and this can be decrypted using the corresponding private key.
The first public key cryptography system was RSA (1977), which was a groundbreaking advancement in the world of cryptography.
RSA is primarily used for encryption, where data is encrypted by anyone using the public key, and decrypted using the private key. However, RSA can also be used for authentication (i.e. digital signatures), where data is encrypted using the private key, and can be decrypted by anyone using the public key.
The first formal proposal for digital signatures was actually DSA (Digital Signature Algorithm) (1991). This uses the same principles of public key cryptography, but was designed specifically for creating digital signatures only.
DSA was improved upon by Schnorr Signatures (1990) and ECDSA (Elliptic Curve Digital Signature Algorithm) (1998). These use the elliptic curve to improve the efficiency of creating and verifying digital signatures.
Public key cryptography can be used for encryption and/or authentication. However, Bitcoin uses the authentication (digital signatures) side of public key cryptography.
Summary
Satoshi didn't invent any new kind of cryptography for use within Bitcoin; they simply utilized existing cryptographic tools to build the first decentralized electronic payment system:
- Hash Function – Used for mining and connecting the blockchain together.
- Digital Signatures (e.g. ECDSA) – Used for locking and unlocking bitcoins in transactions.
It's possible that Satoshi didn't know the internal details of hash functions and public key cryptography. However, this wasn't important, as they knew enough about their properties to be able to combine them in a creative way to develop a system that had not previously existed.
And that was genius enough in itself.
So don't worry if you're not an expert in cryptography and you want to work with Bitcoin, because whilst it's cool to understand how it all works under the hood, it's only important to simply be aware of what tools are available and what they're useful for.
Skill in production cryptanalysis has always been heavily on the side of the professionals, but innovation, particularly in the design of new types of cryptographic systems, has come primarily from the amateurs.
Resources
- Crypto by Steven Levy – This is an excellent book for anyone looking for a light yet deeply interesting introduction to the history of modern cryptography. I highly recommend it.
- Introduction to Cryptography by Christof Paar – Excellent series of lectures explaining the technical details of modern cryptography. Includes videos on hash functions, elliptic curve cryptography, and digital signatures.