Public Keys
What is a public key?
A public key is the counterpart to a private key.
And similar to a private key, it's displayed as a hexadecimal string.
For example:
025980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a418
If we didn't end up shortening this public key to an address, this would be the "account number" that you send bitcoins to when making a transaction.
Anyway, here's the interesting part: your public key is calculated from your private key.
How do you get a public key from a private key?
You insert a private key into a special mathematical function, and the result is a public key.
What is this function?
It's called elliptic curve multiplication.
This basically involves "bouncing" around the graph of an elliptic curve until you end up at a final set of co-ordinates on the graph, and these resulting co-ordinates are your public key.
It'll be easier if I show you...
What does an elliptic curve look like?
Like this:

Furthermore, the elliptic curve used in Bitcoin comes with a specific starting point.
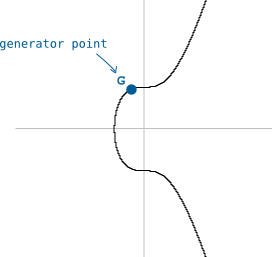
We call this starting point the generator point (G).
And if we were to do some "multiplication" on this curve (e.g. "multiplying" the starting point by 2), we would move around the curve like this.
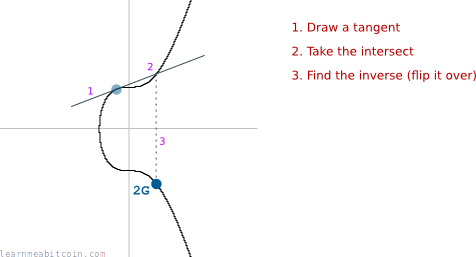
The fact that we can draw a tangent anywhere on the curve and it intersects one other point on the curve is a special feature of elliptic curves.
And there we have it. We have just "multiplied" the starting co-ordinate G by 2, and found the position of the final co-ordinate 2G.
This is one round of elliptic curve multiplication.
Elliptic curve multiplication
I keep putting "multiplication" inside quotes, because multiplication on elliptic curves is not standard multiplication. For example, if you were to multiply the co-ordinates of G by 2, it would not give you the co-ordinates of 2G (as shown on the graph).
You see, the geniuses who found out that you can move around the curve in this specific way had to call it something, so they to decided refer to this operation as "multiplication". Because, you know, mathematics can never be confusing enough.
So when I say "multiplication" from now on, I mean "elliptic curve multiplication".
How do you create a public key?
In the above example we multiplied G by 2 to get 2G.
To get a public key, we multiply G by our private key.
private key = 1daeed97308d028a6724d9d9ca1e998b7df35aac01e8c5848186991da87bb704
private key = 13426143788135298357919653192284501093357630335513137105333560896163591993092
public key = 13426143788135298357919653192284501093357630335513137105333560896163591993092 * G
Or in other words, "bounce around the elliptic curve private key number of times".
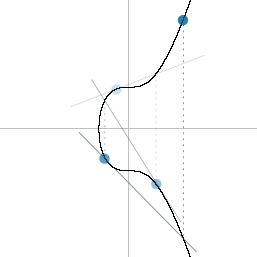
The final resting point on the elliptic curve will give you a set of co-ordinates, and these co-ordinates form the public key.
So if these are the coordinates we end up with after multiplying G by our private key:
x = 40482947186891155689709570640229562463443812510129395065113149778535069557784
y = 58654144176201112664972037427901340718959903893053347826987965270931927657752
Then all we have to do is convert both to hexadecimal and smush them together...
public key (x) = 5980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a418
public key (y) = 81ad11b36aae2360e89168637335dcde77eeb7aaee0f4598069930ef935aed18
public key (x,y) = 5980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a41881ad11b36aae2360e89168637335dcde77eeb7aaee0f4598069930ef935aed18
And ta da! A public key!
Public key format
This is the old (long) format of public key, which means I've got to put an 04 at the start. Like this:
public key = 045980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a41881ad11b36aae2360e89168637335dcde77eeb7aaee0f4598069930ef935aed18
To find out why this is the case, I'm afraid you're going to have to read through the section about compressed public keys.
Compressed Public Keys
To save space, public keys (these days) use the full x coordinate only.
This is because the elliptic curve is an equation (y^2 = x^3 + 7), which means that if you have the x co-ordinate, you can work out the corresponding y co-ordinate.
However, due to the y^2 part of the equation, the y could be a positive or negative number:
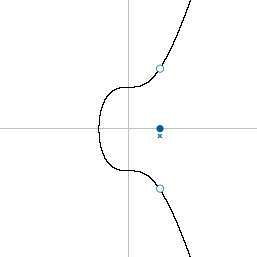
So the only extra information you need to find the correct y co-ordinate is to know whether the y co-ordinate is above or below the x-axis. And due to the way elliptic curves work:
- If
yis even, it's above the x-axis. - If
yis odd, it's below the x-axis.
So instead of having to store both the full x and y co-ordinates, you can just store the full x co-ordinate, and whether the y co-ordinate is even or odd.
In Bitcoin, the polarity of the y co-ordinate is represented by a prefix:
02= even03= odd
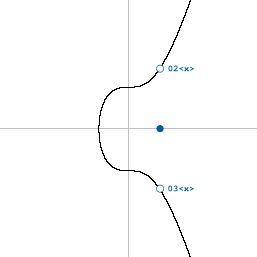
So whereas an old-school uncompressed public key will begin with 04, a compressed public key will begin with either 02 or 03:
public key (uncompressed) = 045980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a41881ad11b36aae2360e89168637335dcde77eeb7aaee0f4598069930ef935aed18
public key (compressed) = 025980893f09241b063f043dc3b523f8c36ccd99f9a8031af861a2cb3ef690a418
Much shorter.
This seems like a lot of effort to save on a small amount of data, but because public keys are used within almost all transactions, it does end up saving a lot of space in the blockchain over time.
Why do we use elliptic curve multiplication to make public keys?
Because elliptic curves have two useful properties when creating a private/public key pair.
- Elliptic curve multiplication is a "trapdoor function". In other words, you can't go backwards from public key to find out what the private key was.
A trapdoor function is a function that is easy to compute in one direction, yet difficult to compute in the opposite direction (finding its inverse) without special information, called the "trapdoor".
-
The public key has a mathematical connection to the private key. As a result, it's possible to prove this connection (with a little more mathematics) without having to reveal your private key.
So if I give you my public key (or address), I can prove to you that I "own" it without having to show you my private key.
This feature is especially handy when making bitcoin transactions. Your public key can be placed into a transaction when you want to receive bitcoins, and you do not have to reveal the private key directly when you want to spend them later on (see digital signatures). As a result, this means that nobody can acquire the private key and use it to spend bitcoins that have been locked to the same public key.
When I say prove that I own a public key, I mean "show that I possess the private key that the public key was created from".
How can you prove you own a public key?
This is a whole topic (or two) in itself. But seeing as this is such an annoyingly relevant question, I'll try my best to cover the basics.
As mentioned, there's a mathematical connection between the private key and public key.
As a result:
- I can put my private key through some more elliptic curve mathematics to get a new value (called a digital signature).
- I can put my public key through some other elliptic curve mathematics to get a new value.
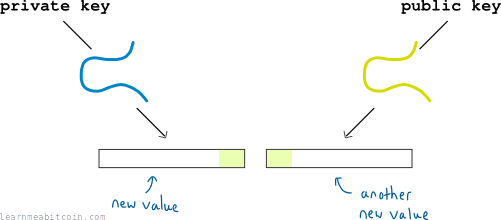
Now, there will be some small overlap between these new values:

And this overlap is enough to prove that there is a mathematical connection between the public key and private key.
And because nobody is able to recreate this digital signature without the private key, my digital signature it's enough to prove that I "own" the public key.
As a result, I can show you that I own a public key with a digital signature, and you never need to see my private key.
Conclusion
All hail the elliptic curve.